The dangers of 'public' SSH Servers
It is widely known that publicly accessible SSH servers pose a significant security risk, particularly if access is not restricted to certain IP addresses or if SSH keys are not used for login. However, many still rely on basic password authentication, assuming that they won’t be targeted by attackers. Unfortunately, this is a false assumption.
Even if you don’t consider yourself a high-profile target, your server can still be vulnerable to cyberattacks.
After collecting some data on one of my servers, I’ve decided to reveal how bad the situation is.
Connections
So let’s have a look at how many people (or better, let’s call them bots) are trying to connect to one of my servers every 15 minutes:
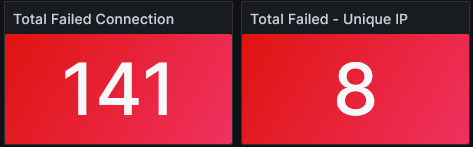
Over 140 failed connections, that’s a lot (considering this is only the last 15 minutes), but luckily most of the bots aren’t smart enough to figure out which operating system I am actually running and so they are trying to login with completely non-sensical usernames.
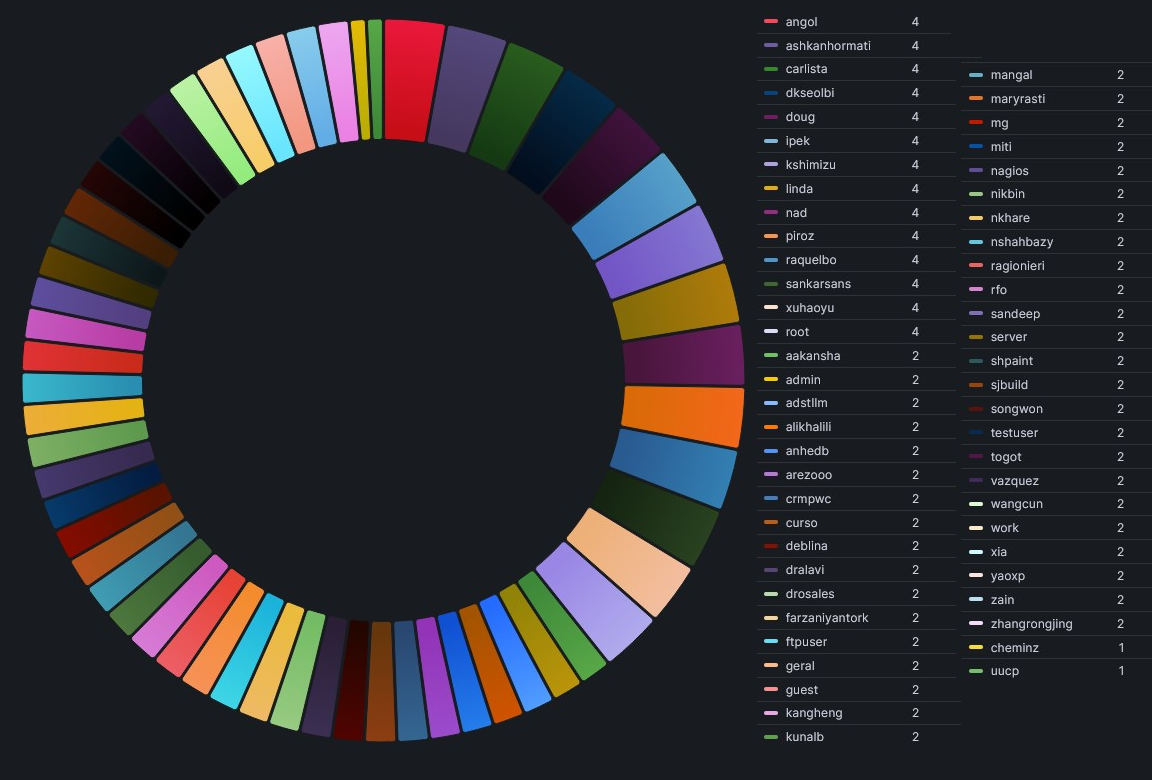
As you can see, those bots rely on poorly written scripts that simply use brute force to attempt every possible username and password until they give up or get locked out.
Where are they coming from?
Now let’s examine the IP Geolocation of these bots. Keep in mind that this is not a complete overview of their origin, as many may use proxies and VPNs for this activity.
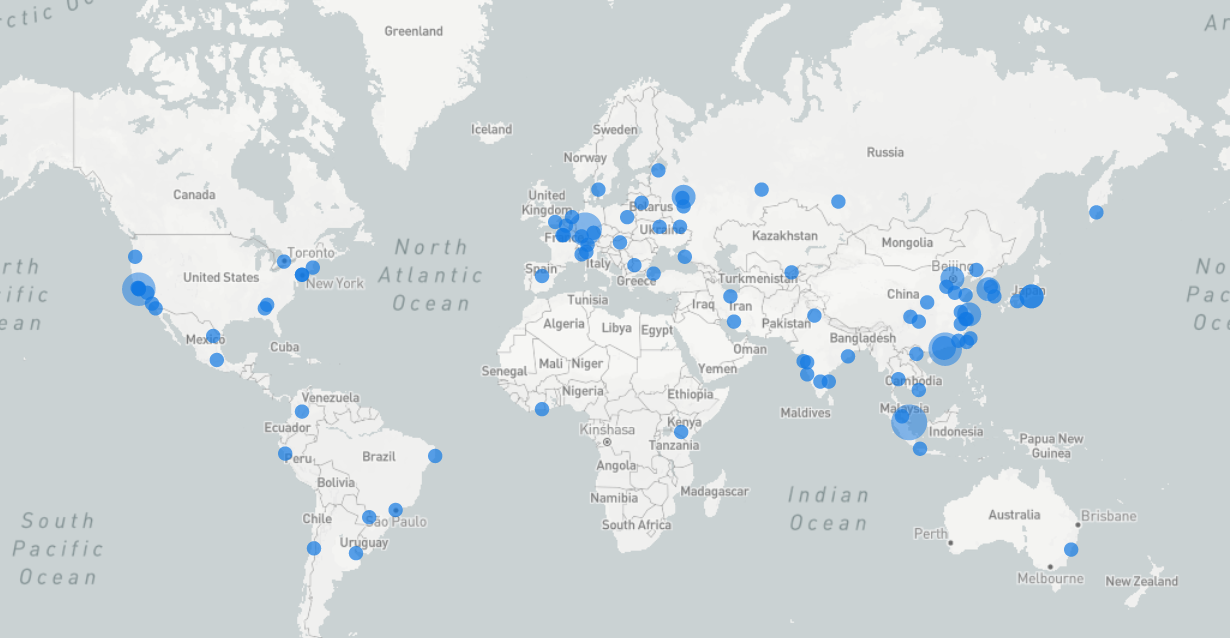
This seems somewhat believable. Many usernames appear to be of Asian origin, and numerous requests come from this region.
This could be because of multiple reasons:
Asia has a significant population, with China being the most populous country in the region.
Many governments in this region do not take responsibility for cyberattacks on foreign infrastructure.
Botnets are a major concern in these countries as many users still use outdated operating systems that are vulnerable to Botnet infections.
Conclusion
"How much at risk is the average person really?"
It all depends on your configuration and setup. The most important thing to protect yourself is to set up a strong password and disable all root remote access. This will likely shield you against most basic attacks. However, it is unclear how bots and scripts will change in the future. Therefore, the best way to secure your server is to use key-based authentication. If you want to take extra precautions, you can limit the IP access to your server or set up a VPN to ensure that no one else can connect to it.